Introduction:
Recently I decided to perform an investigation of a potential phishing email from the phish_pot GitHub page https://github.com/rf-peixoto/phishing_pot. The email I investigated seemed to be impersonating Microsoft alerting a user about malicious activity on their account from Russia.
Analysis:
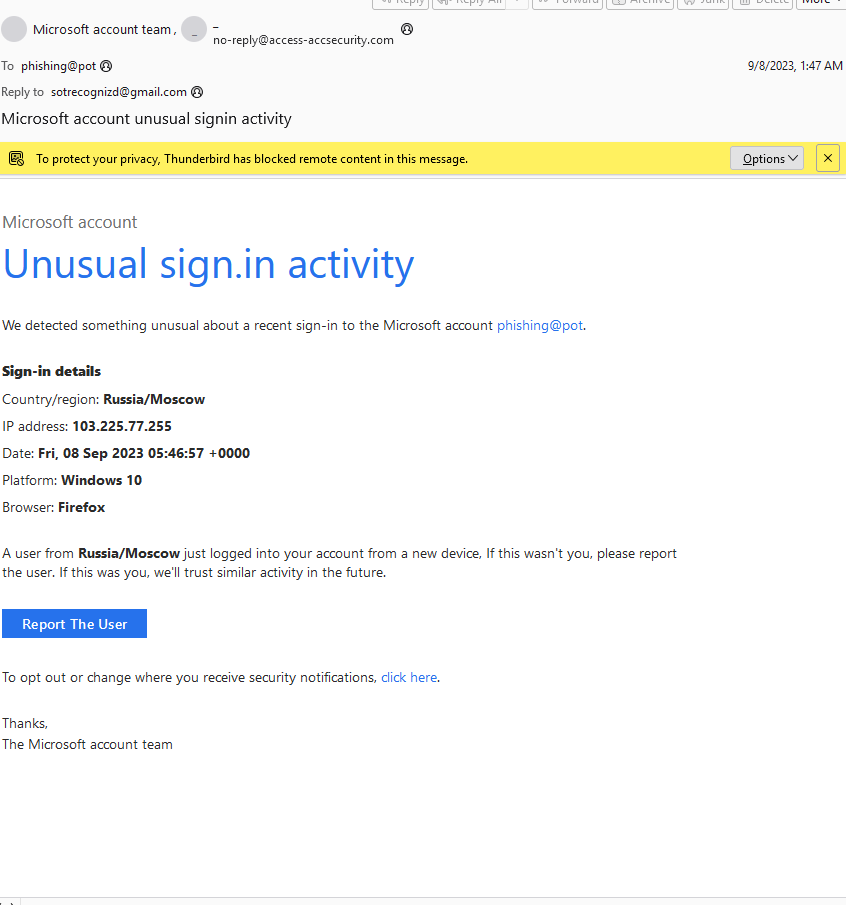
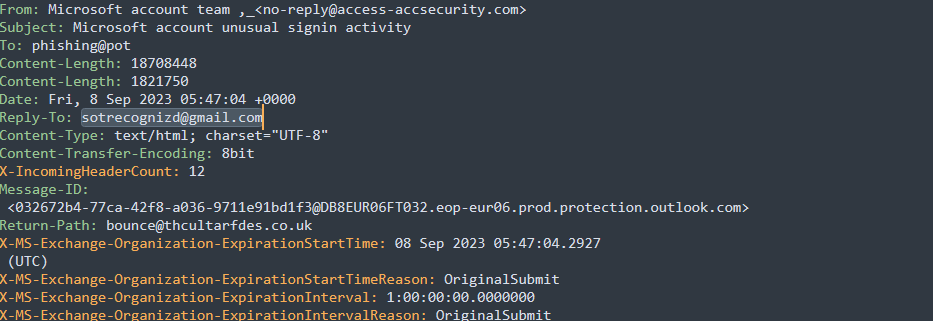
The first thing I did in my investigation was view the meta data of the email by opening the email in sublime text using a plugin to highlight all the headers. The first I noticed was the email in the From header does not use a Microsoft domain. Instead It uses the domain “access-accsecurity.com”. After running a domain search I found that this domain is not associated with Microsoft.
The second suspicious thing I noticed was the difference between the From and Reply-to headers. The From header contained the email “no-reply@access-accsecurity.com” while the Reply-to header contained “sotrecognizd@gmail.com”. This is not necessarily suspicious, many organizations use a different Reply-to email from the From email, however, having two different email domains for the From and Reply-to headers is suspicious especially when the Reply-to email uses the gmail.com domain which Microsoft does not use.
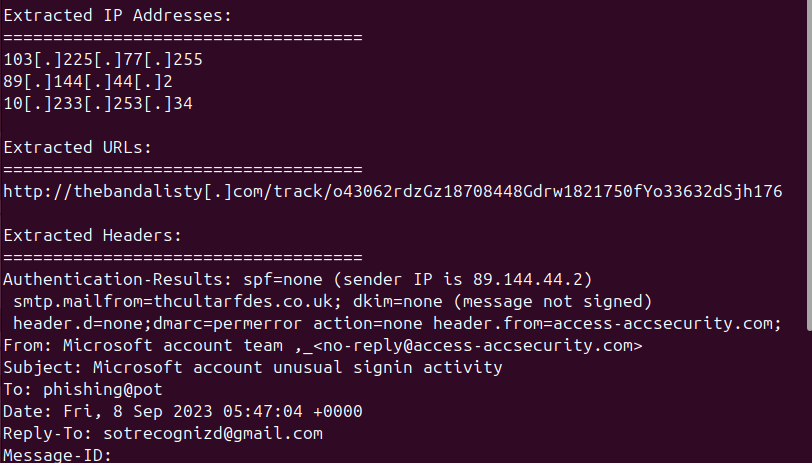
After that analysis I extracted all embedded URLs and IP addresses from the email using a python script called eioc.py which extracts IPs and URLs and displays them in defanged format (defanged format is a way of displaying URLs and IPs which does not allow you to accidently navigate to those addresses making it safer to investigate). There were three IPs and one URL. Investigating the IP
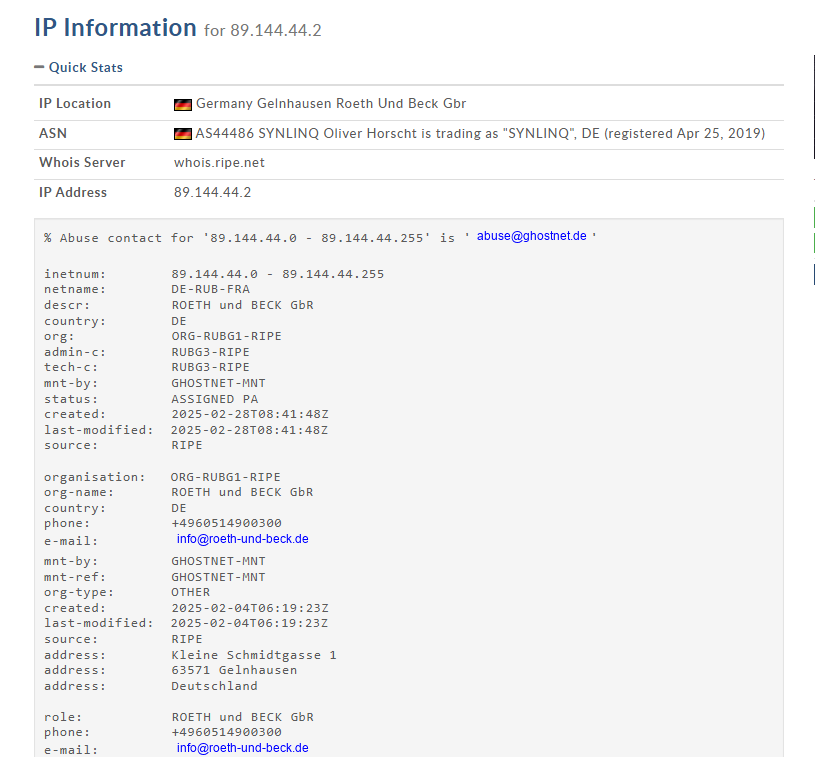
The only IP address that presented any interesting information was the address shown in the Received headers 89[.]144[.]44[.]2, running a whois search on this address showed that it originates from Germany
very suspicious for a US company like Microsoft. Running a VirusTotal search on the extracted URL revealed that it may be associated with Phishing attacks, however, the domain was taken down before I could do more in depth analysis of the domain using a sandbox.
The email contained a button to report the user, however, all that button does is start an email with the gmail.com email address listed in the meta data. I believe that this email is meant to use Familiarity with a know company like Microsoft along with the Urgency of a potential account breach to convince the victim to begin an email exchange with the attacker to continue the scam. This could lead to the scammer using social engineering techniques to gain confidential information from the victim or convince the victim to purchase gift cards ( A popular form of currency in online scams) for the attacker.
Conclusion:
After my investigation I concluded that this email is indeed malicious and is most likely an attempt to gain confidential information from the victim. These phishing attempts can mitigated by validating the From and Reply-to headers, not clicking any links in emails that are suspicious, and using an IPS or firewall to add these types of emails to a block list.
There are always people out there looking to scam and steal from you so its important to educate yourself on these phishing techniques to stay safe in the virtual world.
Writeup:
Headers
Date: Fri, 8 Sep 2023 05:47:04 +0000
Subject: Microsoft account unusual signin activity
To: phishing@pot
From: Microsoft account team ,_no-reply@access-accsecurity.com
Reply-To: sotrecognizd@gmail.com
Return-Path: bounce@thcultarfdes.co.uk
X Sender IP: 89.144.44.2
Message-ID: 032672b4-77ca-42f8-a036-9711e91bd1f3@DB8EUR06FT032.eop-eur06.prod.protection.outlook.com
URLs
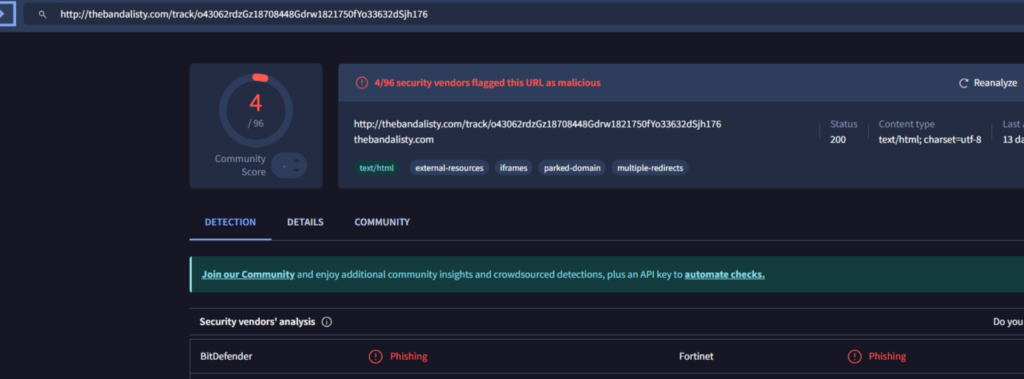
hxxp://thebandalisty[.]com/track/o43062rdzGz18708448Gdrw1821750fYo33632dSjh176
Extracted IPs’
103[.]225[.]77[.]255
89[.]144[.]44[.]2
10[.]233[.]253[.]34
Description
The received email appears to be from Microsoft alerting the user to unusual activity on their Microsoft account from a Russian IP address. The email includes a link to report the user near the bottom of the email.
Artifact Analysis
Sender Analysis: After analyzing the X Sender-IP it was determined that the IP originated from Germany. The sender domain (access-accsecurity.com) is not associated with Microsoft and appears to be associated with a phishing campaign according to a VirusTotal search.
URL Analysis: The URL hxxp://thebandalisty[.]com/track/o43062rdzGz18708448Gdrw1821750fYo33632dSjh176 appears to not be accessible anymore, and was associated with a phishing campaign according to a VirusTotal search.
Verdict
The Reply email address uses the gmail.com domain which is not associated with Microsoft.com. The IP address that was claimed to be from Russia is actually from India. The extracted IP addresses are associated with a phishing campaign. In conclusion, the received email has been deemed illegitimate.
Defense Actions
- Block all emails from the address no-reply@access-accsecurity.com, additionally block the email sotrecognizd@gmail.com.
- Investigate the extent of this phishing campaign and block all associated IP addresses.
- Continue user training on avoiding being compromised by phishing emails.
