After being interested in and studying cybersecurity for a while I have decided to actually post some of the things I’ve learned and some of the projects that I have been working on for the past few months.
The first thing I wanted to do was set up a SIEM solution for my home network implementing a DNS blocker, IPS, and a log indexer. All solutions would have to be compatible with pfsense since that is what I chose as my network firewall. Because of this I settled on pfblockerng for my DNS blocker, Snort for my IPS, and SPLUNK for my log indexer.
For this post I’m going to focus exclusively on pfblockerng and all the lessons learned from setting up a DNS blocker.
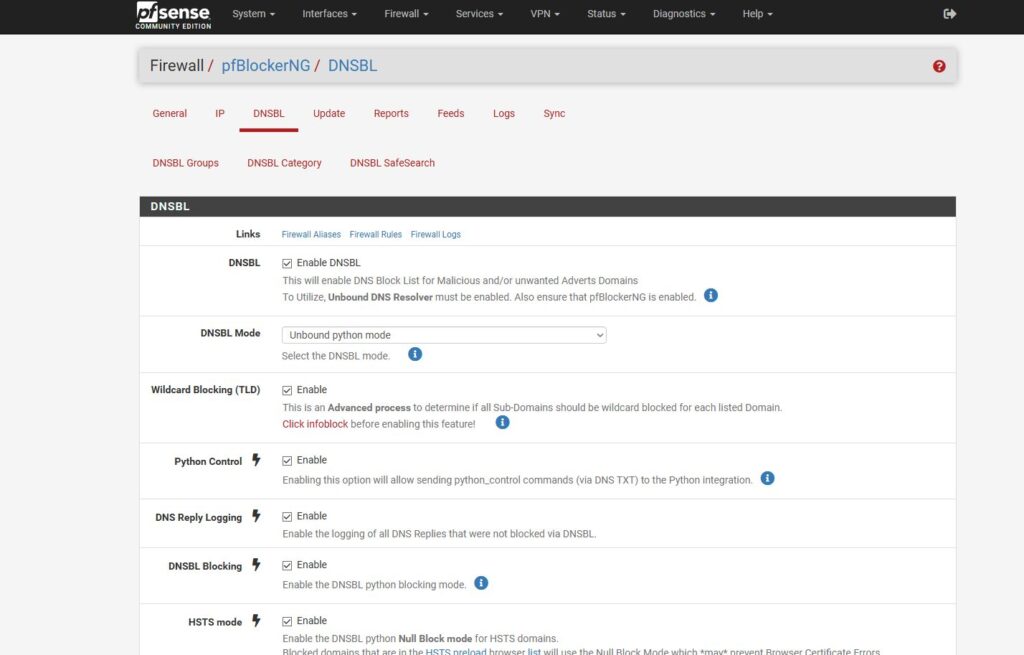
The service was easy enough to install on pfsense, simply download the pfblockerng package for the pfsense instance and enable both pfblockerng and DNSBL in the configuration settings.
However, I wanted to go a bit further than this. Pfblockerng also has different DNSBL feeds that can be added which will further increase the amount of known malicious domains blocked by pulling from a trusted database. The feed I chose was from phishtank https://lnkd.in/e2-mSYUN.
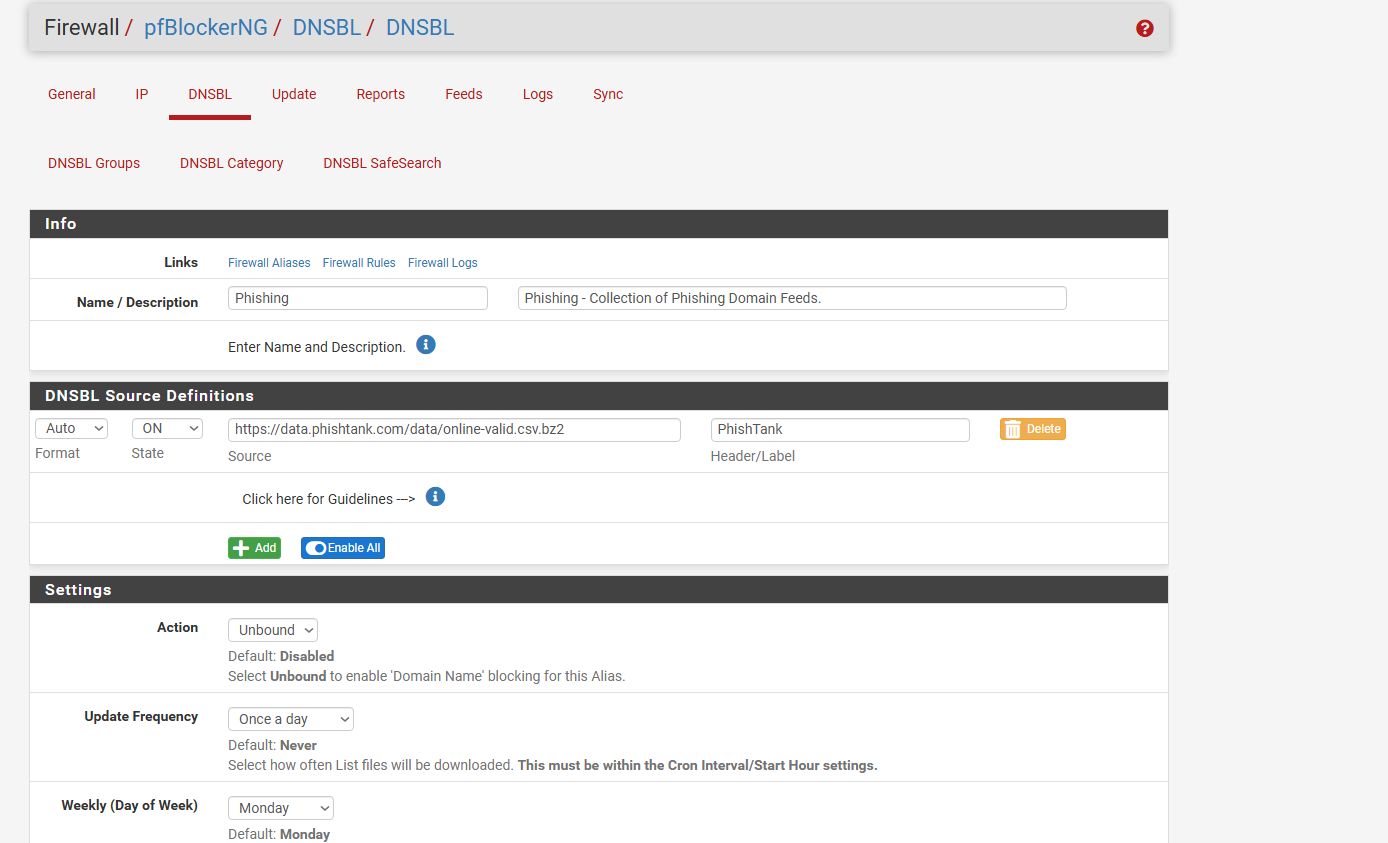
So I added the feed and it worked instantly and required no configuring right? WRONG! My family noticed they couldn’t access certain websites on our network such as LinkedIn.com, drive.google.com drive and much more. To fix this issue I had to create a whitelist and whitelist all domains we normally use along with any subdomains associated with the TLD. It turns out that the phishtank feed adds domains based on known phishing attacks, because of this a lot of normally non-malicious domains such as drive.google.com were added to the repository. Attackers will sometimes use known reputable domains and services in their attacks. This is why in any investigation it should be determined if the TLD is a know non-malicious domain and if the TLD is critical to the functions for the network before the decision to block the domain is made. After a lot of configuration and whitelisting I finally got my network back to its normal day to day functionality. However, I still wanted more security, so I decided to add an IPS to my network, but that story is for another time.
Cybersecurity is very fun and interesting and I’m learning more and more every day. However, just learning and reading isn’t enough which is why I decided to implement what I’ve learned in projects and network building. I hope to learn from these projects and hope to learn more from people who have been doing this a lot longer than me.
That’s all from me today. Until next time!!
